The AI Security Challenge for Enterprise Applications
AI Security in Proggio addresses the challenges of integrating artificial intelligence into enterprise project management applications.
It ensures robust protection for sensitive data and compliance with industry standards.
AI-powered features, from natural language processing to predictive analytics, introduce new attack vectors.
However, traditional security frameworks cannot fully address these data protection concerns.
Enterprise project management platforms handle sensitive strategic information, resource allocations, and confidential business data, making them particularly vulnerable.
The core challenges include protecting proprietary data from exposure during AI model interactions.
They also include ensuring secure API connections between enterprise systems and AI services.
Organizations must maintain data sovereignty and compliance across different jurisdictions.
Another challenge is preventing unauthorized access to AI-powered insights that could reveal competitive intelligence.
Most critically, they must ensure that customer data is never used to train AI models.
Organizations benefit from AI’s transformative power.
At the same time, they must maintain strong security postures to meet regulations and protect stakeholder trust.
Securing AI Without Platform Lock-In: Industry-Standard Approaches
Enterprises can achieve robust AI security through proven, platform-agnostic methods that don’t require commitment to a single vendor ecosystem.
These approaches provide defense-in-depth protection while maintaining flexibility and control over AI implementations.
Multi-Factor Authentication (MFA)
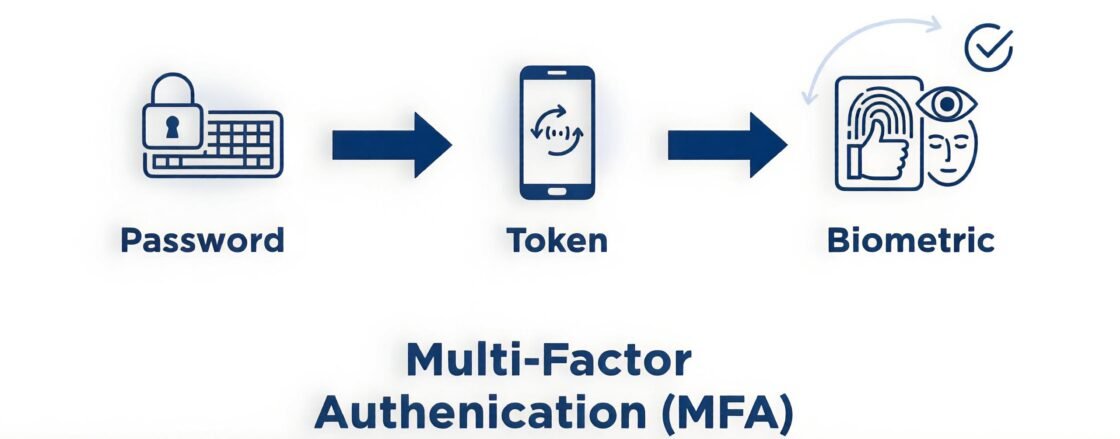
represents the foundational security layer for any AI-enabled application.
By requiring multiple verification factors—something the user knows (password), something they have (security token or mobile device), and potentially something they are (biometric verification)—organizations dramatically reduce unauthorized access risks.
Modern MFA solutions support adaptive authentication, analyzing user behavior patterns and contextual factors to determine when additional verification is needed.
Industry standards like TOTP (Time-based One-Time Password) and FIDO2 provide secure, interoperable authentication across platforms.
API Security and Encryption form the critical backbone of AI security.
Organizations should implement OAuth 2.0 or similar token-based authentication protocols, ensuring that API connections between applications and AI services remain encrypted and authenticated.
Organizations must encrypt all data in transit with TLS 1.2 or higher and at rest using industry-standard algorithms like AES-256.
API gateways provide additional security layers by monitoring traffic patterns, rate limiting requests to prevent abuse, and logging all interactions for audit purposes.
Data Loss Prevention (DLP)
Policies monitor and control what information users can send to AI services, preventing inadvertent exposure of sensitive data.
Organizations should implement content filtering that scans prompts and responses for sensitive information like credentials, personally identifiable information (PII), financial data, and proprietary business information before they reach external AI services.
Access Control and Least Privilege
Principles ensure users only access the AI capabilities and data relevant to their roles.
Role-Based Access Control (RBAC) enables granular permission management, while Single Sign-On (SSO) integration with enterprise identity providers like Okta, Azure AD, or Google Workspace streamlines authentication while maintaining security.
Organizations should implement session timeout policies, IP whitelisting where appropriate, and detailed audit logging that can be exported to Security Information and Event Management (SIEM) systems.
Regular Security Assessments
Including penetration testing, vulnerability scanning, and compliance audits help identify weaknesses before malicious actors can exploit them.
Third-party security certifications such as SOC 2 Type II, ISO 27001, and industry-specific standards (HIPAA for healthcare, PCI DSS for payment processing) provide independent validation of security controls.
Zero-Trust Architecture
Represents the modern security paradigm where no service or user is inherently trusted. This approach includes continuous identity verification, micro segmentation of network access, and the principle of least privilege access.
For AI applications, this means every request is authenticated and authorized, regardless of whether it originates inside or outside the corporate network.
Azure AI Foundry: An Alternative for Microsoft-Centric Organizations
For organizations already deeply invested in the Microsoft ecosystem, Azure AI Foundry (formerly Azure AI Studio) offers a comprehensive, integrated security framework.
This platform provides access to multiple AI models from OpenAI, Anthropic (Claude Sonnet 4.5, Opus 4.1, and Haiku 4.5), Cohere, and over 11,000 other models—all within a unified security environment.
Azure AI Foundry’s security architecture includes network isolation through private endpoints where public access can be disabled entirely, Azure Role-Based Access Control with Microsoft Entra ID for granular permissions, customer-managed encryption keys for regulatory compliance, and a zero-trust architecture where no component assumes inherent safety.
Microsoft performs security investigations on models before hosting them and continuously monitors for changes impacting trustworthiness.
Critically for enterprise security, Microsoft maintains strict data boundaries in Azure AI Foundry.
Microsoft does not use customer prompts or outputs to train its foundational AI models.
All AI models operate within customer tenant boundaries with no runtime connections to external model providers, ensuring data remains under organizational control.
However, Azure AI Foundry is most appropriate for organizations already using Azure infrastructure extensively.
For companies using diverse cloud environments or preferring vendor flexibility, the platform-agnostic security approaches described earlier provide equivalent protection without ecosystem lock-in.
Leading LLM Vendors' Commitment to Data Privacy
A critical security consideration when selecting AI services is whether customer data will be used to train AI models.
Importantly, leading enterprise AI providers have made explicit commitments to protect customer data from being incorporated into model training—a crucial safeguard for proprietary business information.
OpenAI’s Enterprise Privacy Commitment
OpenAI’s enterprise services—including ChatGPT Business, ChatGPT Enterprise, and the API platform—operate under strict privacy policies where customer data is not used to train models by default.
Their security framework includes:
- Data Ownership: Organizations own their business data entirely—it remains confidential, secure, and under complete customer control
- Encryption Standards: AES-256 encryption at rest and TLS 1.2+ in transit, with Enterprise Key Management (EKM) options for customers to control their own encryption keys
- Zero Data Retention: Qualifying API customers can configure zero data retention policies
- Compliance Support: SOC 2 Type 2, ISO 27001 certification, GDPR and CCPA compliance support, and Business Associate Agreements (BAA) for HIPAA compliance
- Data Residency: Options for data storage in multiple regions including US, Europe, UK, Japan, Canada, South Korea, Singapore, Australia, India, and UAE
OpenAI explicitly states: “We do not train on your business data or conversations, and our models don’t learn from your usage” for enterprise customers.
Claude (Anthropic) Privacy Commitment
Anthropic takes an equally strong stance on data privacy for commercial users. By default, Anthropic will not use inputs or outputs from commercial products such as Claude for Work, Anthropic API, and Claude Gov to train models. Their comprehensive security includes:
- No Training on Commercial Data: Commercial customers maintain complete control as data controllers, and Anthropic does not use shared data to train models unless customers explicitly opt into development partnership programs
- Encryption: Automatic encryption in transit and at rest, with TLS protection for all network communications
- Zero Data Retention (ZDR): Optional ZDR addendum for enterprise customers that eliminates stored records entirely, with requests scanned in real-time and immediately discarded
- Compliance Certifications: SOC 2 Type II, ISO 27001, GDPR compliance, with BAA options for HIPAA requirements
- Access Controls: SAML 2.0 and OIDC-based SSO, domain capture for workspace enrollment, and role-based permissions
- Advanced Security Features: Network isolation options, audit trails for compliance monitoring, and content filtering for high-risk prompts
Anthropic’s commercial terms make clear that customers own all outputs from using Claude models, and Anthropic does not obtain any rights to customer content.
The Critical Distinction: Consumer vs. Commercial Accounts
It’s essential to understand that these no-training commitments apply specifically to commercial and enterprise accounts.
Consumer-tier accounts (including “Pro” accounts from some providers) may have different data usage policies.
Organizations must ensure they’re using appropriate commercial licenses for business use to receive these data protection guarantees.
Proggio's AI Security Standards
Proggio’s AI Security Architecture
Proggio, as an AI-powered project portfolio management platform, implements comprehensive security measures specifically designed for enterprise deployments while leveraging these leading LLM providers’ enterprise-grade protections.
Proggio AI Security Commitment
At Proggio, data protection is paramount.
Proggio AI leverages OpenAI and Claude’s advanced enterprise technology to deliver project management solutions while adhering to the highest standards of data security and privacy.
The platform’s AI security framework includes:
Comprehensive Privacy Measures: Proggio utilizes stringent enterprise API privacy policies designed to protect sensitive information and comply with global data protection regulations.
By using only enterprise-tier LLM services, Proggio ensures customer project data receives the same no-training guarantees provided by OpenAI and Claude to their commercial customers.
Leading LLM Security Integration: Proggio integrates exclusively with leading LLM vendors who maintain robust security commitments.
This includes:
- OpenAI Enterprise Security: State-of-the-art encryption, secure data storage, rigorous access controls, and the explicit commitment that “We do not train our models on your organization’s data by default”
- Claude (Anthropic) Enterprise Security: Comprehensive privacy protections with the clear policy that “By default, we will not use your inputs or outputs from our commercial products to train our models”
No Training on Customer Data: Proggio uses only enterprise-grade API connections to OpenAI and Claude. This ensures that project data, strategic plans, resource allocations, and business information never train AI models.
This protection extends throughout the entire data lifecycle.
Robust Security Framework: Leading LLM vendors’ commitment to security ensures data protection from unauthorized access and cyber threats through enterprise-grade encryption, secure data storage, and rigorous access controls.
Proggio Platform Security
Beyond AI-specific protections, Proggio operates on Salesforce’s Heroku platform, providing an enterprise-grade infrastructure foundation with multiple security layers.
Enterprise Infrastructure: Heroku operates on AWS infrastructure within ISO 27001 and FISMA certified data centers, providing physical security controls and environmental protections.
The platform maintains SOC 1, SOC 2, and SOC 3 attestations, validating security controls through independent audits.
Compliance Certifications: Proggio’s infrastructure supports multiple compliance frameworks:
- GDPR compliance for European data privacy with data minimization, purpose limitation, and user rights management
- HIPAA compliance support through Business Associate Addendum agreements for healthcare organizations
- PCI DSS Level 1 certification for applications handling payment card data
Data Protection Measures:
- Transport encryption using TLS 1.2 or higher for all client-server communications
- Industry-standard firewalls protecting against network-based attacks
- Access control mechanisms enabling organizations to define user permissions and roles
- Container isolation through Heroku’s dyno architecture providing logical separation between customer applications
Data Residency Options
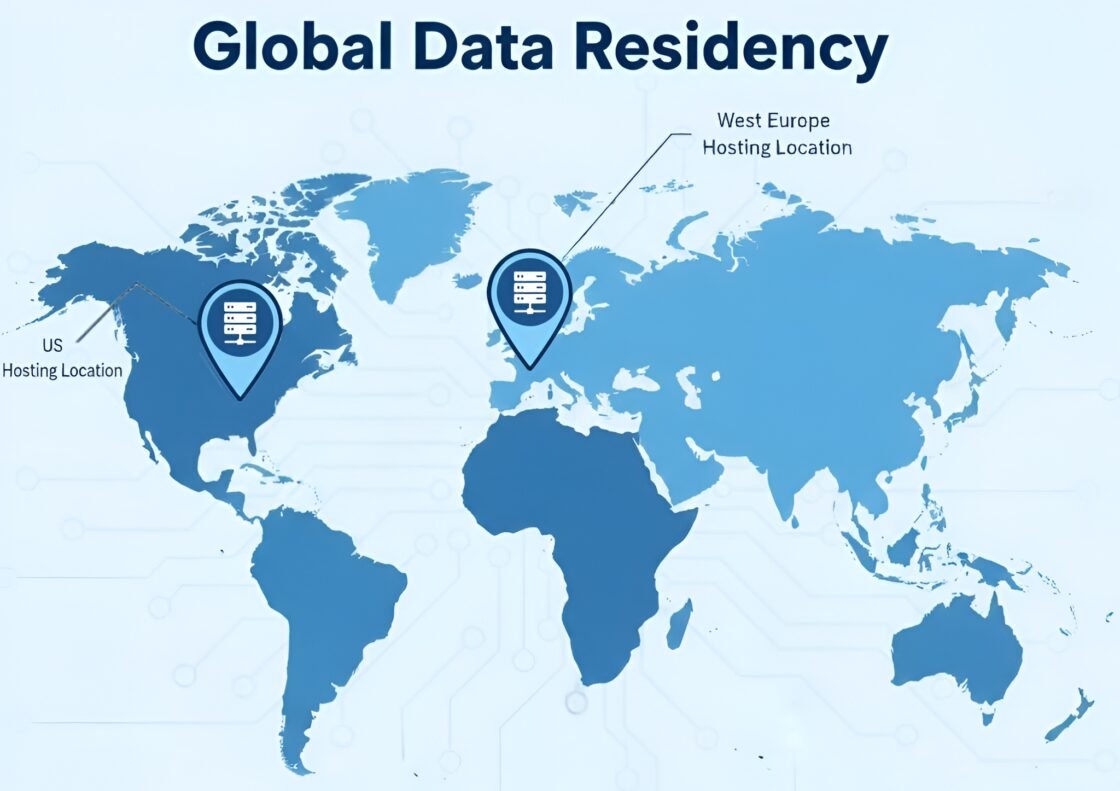
The platform maintains data in West Europe and US locations, allowing organizations to select server locations addressing data sovereignty concerns and compliance requirements.
Authentication and Identity: Built-in authentication controls verify user identities before granting access to project data and AI-powered insights.
The platform should support (and organizations should verify with Proggio) modern authentication options including multi-factor authentication and single sign-on integration.
Alignment with Security Standards
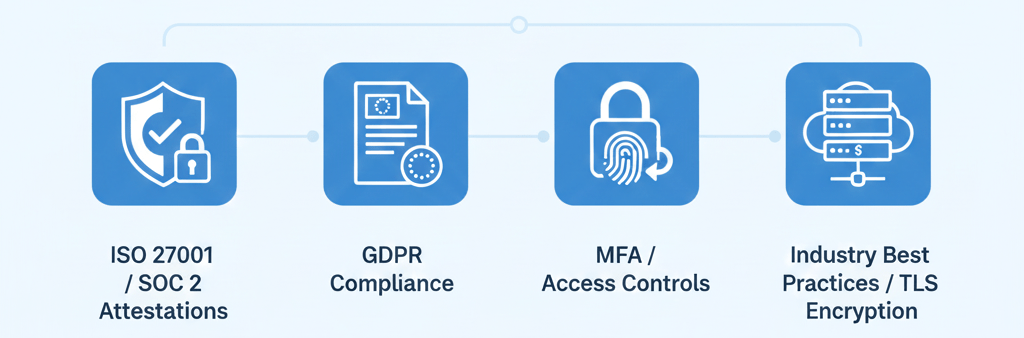
Several key frameworks validate Proggio’s current security posture:
ISO 27001: The Heroku infrastructure’s ISO 27001 certification provides systematic information security management.
SOC 2: The platform’s SOC attestations validate controls for security, availability, and confidentiality — critical for enterprise trust.
GDPR: Compliance measures address European data protection requirements, though organizations should verify specific GDPR controls relevant to their use cases.
Industry Best Practices: The use of TLS encryption, access controls, and enterprise-tier LLM APIs aligns with current security best practices.
Validation Recommendations for Organizations
When evaluating Proggio for deployment, organizations should:
- Verify LLM Usage: Confirm with Proggio that only enterprise-tier APIs are used for OpenAI and Claude services, ensuring no-training guarantees apply.
- Review Data Flow: Understand exactly how project data flows through the system and which components interact with external AI services.
- Assess Authentication: Evaluate whether Proggio’s current authentication options meet organizational requirements, particularly for SSO and MFA.
- Compliance Mapping: Map Proggio’s security controls to specific regulatory requirements applicable to your industry (HIPAA, GDPR, SOC 2, etc.).
- Audit Capability: Confirm that audit logging meets organizational requirements for compliance and security monitoring.
- Incident Response: Review Proggio’s incident response procedures and ensure they align with organizational security policies.
- Data Residency: Verify that available data center locations meet your data sovereignty requirements.
- Contract Terms: Ensure that security commitments, including no-training guarantees and data ownership, are explicitly included in service agreements.
Conclusion
AI security in enterprise applications requires a layered approach using platform protections, application-specific controls, and strong organizational policies.
The most critical security consideration for AI-powered platforms is ensuring customer data is never used to train AI models — a commitment that leading providers like OpenAI and Claude have made for their enterprise customers.
Proggio’s security architecture benefits from leveraging these enterprise-grade LLM services while operating on the robust Heroku/Salesforce infrastructure.
Additionally, the platform’s combination of compliance certifications, encryption standards, and enterprise-tier AI provider relationships provides a solid security foundation for organizations seeking AI-powered project management capabilities.
Whether implementing security through comprehensive platforms like Azure AI Foundry or through platform-agnostic approaches using MFA, API security, and access controls, enterprises must prioritize several key principles:
- Data sovereignty: Ensuring customer data is never used for AI training and remains under organizational control
- Defense in depth: Multiple security layers protecting against different threat vectors
- Continuous compliance: Regular auditing and validation against regulatory requirements
- Transparent communication: Clear documentation of security measures, data handling practices, and incident response procedures
- Adaptive security: Continuous enhancement to address emerging threats and evolving best practices
- User empowerment: Training and tools that enable users to work securely with AI
Organizations evaluating AI-powered tools like Proggio should assess not only current security capabilities but also the vendor’s commitment to ongoing security enhancement, responsiveness to emerging threats, and alignment with industry best practices.
The most successful deployments combine robust platform security with strong organizational policies and user education, creating an environment where AI’s transformative potential is fully realized while enterprise data remains protected.
By integrating leading LLM providers’ advanced enterprise technology with comprehensive platform security, Proggio enables organizations to access data-protected, AI-based project management capabilities, allowing them to focus on what matters most—delivering successful projects.